.+:::::::::::::::::::::::::::::::::::::::::/
.//`+++++++++++++++++++++++++++++++++++++// s
-+/.h+..................................-os s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h/ ss s
-+/.h+ ss s
-++-yo////////////////////////////////////y`s
-+o-:--------------------------::::-:://:---s
-+/ :-.: +:oo- s
-+/```````````````````````````````````:-````s
./o//////////+o:::::::::::::::::s+/////////::
``://////////+s:::::::::::::::::y+/////////:.
s .::::/osso::::. .+
`.y +yyyyhNNNmyyyy+ .+
`:h:::::/+:::::::::::::+:///////////////////+--------------------
.o s s::::::::::::s.+ - +
-/y .o s ::::::::::::oss+::.+
`-y .o y `+//: .+
`.+/y/::/+:::::::::::::+:::::::::::::::::++:.
`////////////////////////////////////:/.
Structures and logic can serve as artistic material.
However, not their visually perceptible form, as expressed in abstract painting, but their invisible and abstract essence in itself.
The structure and logic as such can be experienced through art.
A system consists of boundaries.
They are like contours, without which the delimited and categorized states would not be perceptible.
Digital information is nothing but an indeterminable sea of ones and zeros.
Only the systems structures makes it possible to give meaning to the bits.
Somewhat more generally phrased, a system is the inherent desire of human beings to search for artificial and natural patterns,
orders and connections and to never finally find them in a meaningless universe, because everything is constantly changing.
This leads to a single concluson:
Where there are boundaries, action can be taken against them.
__ ___ ___ __
/\ | | |__) \ / | |__ /__`
/~~\ |___ |___ |__) | | |___ .__/
__ ___ __ __ ___ ___ ___ __
/\ |__) |__ / ` |__) |__ /\ | |__ | \
/~~\ | \ |___ \__, | \ |___ /~~\ | |___ |__/
___ __
|__ / \ | | /\ |
|___ \__X \__/ /~~\ |___
Let's dive into the ocean of bytes.
Since the binary system is difficult for humans to read and therefore not necessarily suitable for direct interaction,
an encoding is needed that makes it possible to better represent binary numbers.
For this purpose, eight bits are combined into one byte and converted into the hexadecimal notation.
The hexadecimal system makes it possible to translate a long and confusing series of bits (00110000) into a shorter representable number (30).
To the numbers 0 to 9 from the decimal system the letters A to F are added (0123456789ABCDEF).
This results in 16 possible numbers and therefore perfectly complements the dual binary system to represent a byte.
A byte with 255 possible values can be represented with the numbers 00 to FF.
Hexadecimal 00 is 0000 0000 in bits and hexadecimal FF is 1111 1111. For example, a part of a binary file would look like this:
68 61 63 6b 69 6e 67 2e 61 72 74
Some bytes within a certain value range can be converted again into another state, namely into printable characters, for example letters.
The row of bytes shown here would result in the string hacking.art if converted.
This translation of bytes into letters is only possible because it was agreed upon by means of the American Standard Code for Information Interchange (ASCII).
The standard defines which letters should be represented by which bits.
But in the end it's just a table where we can find the corresponding hexadecimal values.
__ __
/\ /__` / ` | |
/~~\ .__/ \__, | |
___ __ ___
| /\ |__) | |__
| /~~\ |__) |___ |___
Oct Dec Hex Char Oct Dec Hex Char
────────────────────────────────────────────────────────────────────────
000 0 00 NUL '\0' (null character) 100 64 40 @
001 1 01 SOH (start of heading) 101 65 41 A
002 2 02 STX (start of text) 102 66 42 B
003 3 03 ETX (end of text) 103 67 43 C
004 4 04 EOT (end of transmission) 104 68 44 D
005 5 05 ENQ (enquiry) 105 69 45 E
006 6 06 ACK (acknowledge) 106 70 46 F
007 7 07 BEL '\a' (bell) 107 71 47 G
010 8 08 BS '\b' (backspace) 110 72 48 H
011 9 09 HT '\t' (horizontal tab) 111 73 49 I
012 10 0A LF '\n' (new line) 112 74 4A J
013 11 0B VT '\v' (vertical tab) 113 75 4B K
014 12 0C FF '\f' (form feed) 114 76 4C L
015 13 0D CR '\r' (carriage ret) 115 77 4D M
016 14 0E SO (shift out) 116 78 4E N
017 15 0F SI (shift in) 117 79 4F O
020 16 10 DLE (data link escape) 120 80 50 P
021 17 11 DC1 (device control 1) 121 81 51 Q
022 18 12 DC2 (device control 2) 122 82 52 R
023 19 13 DC3 (device control 3) 123 83 53 S
024 20 14 DC4 (device control 4) 124 84 54 T
025 21 15 NAK (negative ack.) 125 85 55 U
026 22 16 SYN (synchronous idle) 126 86 56 V
027 23 17 ETB (end of trans. blk) 127 87 57 W
030 24 18 CAN (cancel) 130 88 58 X
031 25 19 EM (end of medium) 131 89 59 Y
032 26 1A SUB (substitute) 132 90 5A Z
033 27 1B ESC (escape) 133 91 5B [
034 28 1C FS (file separator) 134 92 5C \ '\\'
035 29 1D GS (group separator) 135 93 5D ]
036 30 1E RS (record separator) 136 94 5E ^
037 31 1F US (unit separator) 137 95 5F _
040 32 20 SPACE 140 96 60 `
041 33 21 ! 141 97 61 a
042 34 22 " 142 98 62 b
043 35 23 # 143 99 63 c
044 36 24 $ 144 100 64 d
045 37 25 % 145 101 65 e
046 38 26 & 146 102 66 f
047 39 27 ' 147 103 67 g
050 40 28 ( 150 104 68 h
051 41 29 ) 151 105 69 i
052 42 2A * 152 106 6A j
053 43 2B + 153 107 6B k
054 44 2C , 154 108 6C l
055 45 2D - 155 109 6D m
056 46 2E . 156 110 6E n
057 47 2F / 157 111 6F o
060 48 30 0 160 112 70 p
061 49 31 1 161 113 71 q
062 50 32 2 162 114 72 r
063 51 33 3 163 115 73 s
064 52 34 4 164 116 74 t
065 53 35 5 165 117 75 u
066 54 36 6 166 118 76 v
067 55 37 7 167 119 77 w
070 56 38 8 170 120 78 x
071 57 39 9 171 121 79 y
072 58 3A : 172 122 7A z
073 59 3B ; 173 123 7B {
074 60 3C < 174 124 7C |
075 61 3D = 175 125 7D }
076 62 3E > 176 126 7E ~
077 63 3F ? 177 127 7F DEL
As you can see it is divided into the columns Oct, Dec, Hex and Char.
Char is the human readable letter and Hex is the number that is processed in the computer internally.
Furthermore there are a number of special characters (NUL, CR, LF) and not all bytes from 0 to 255 or 00 to FF are also an ASCII character.
Therefore there are "non-printable" bytes.
HINT: In a Linux console, this ASCII table can be invoked with the command: man ascii
The small excursion to the hexadecimal system is only to understand the following part better.
You only have to remember: In the computer everything consists of bytes, no matter in which notation they are read.
___ ___
|__ | | |__
| | |___ |___
__ ___ __ __ ___ __ ___ __
/__` | |__) | | / ` | | | |__) |__ /__`
.__/ | | \ \__/ \__, | \__/ | \ |___ .__/
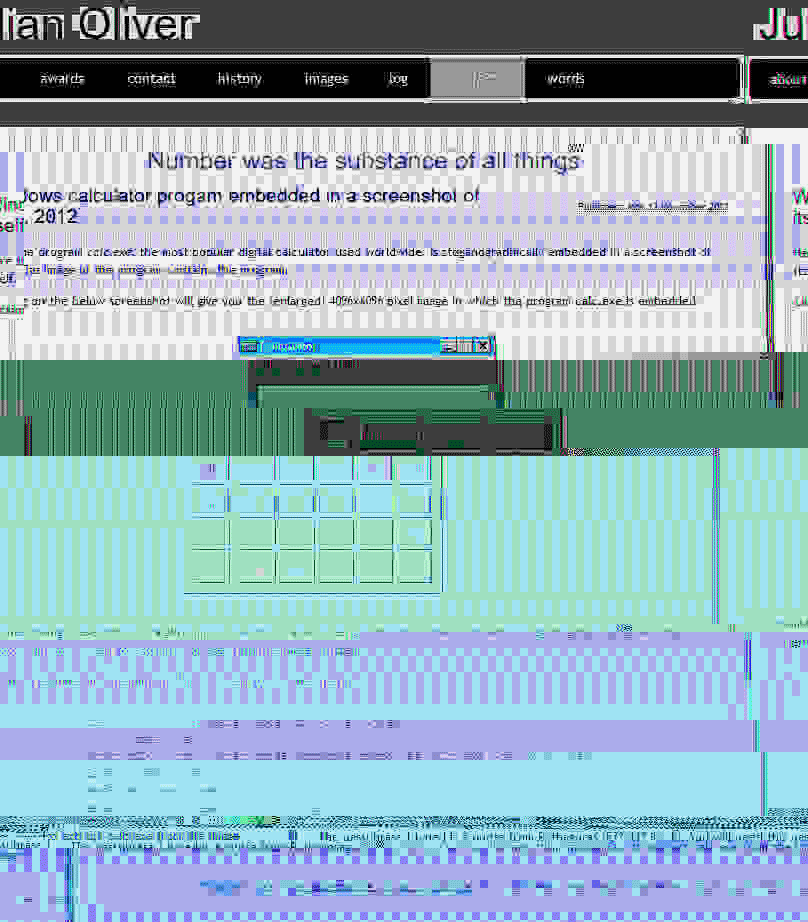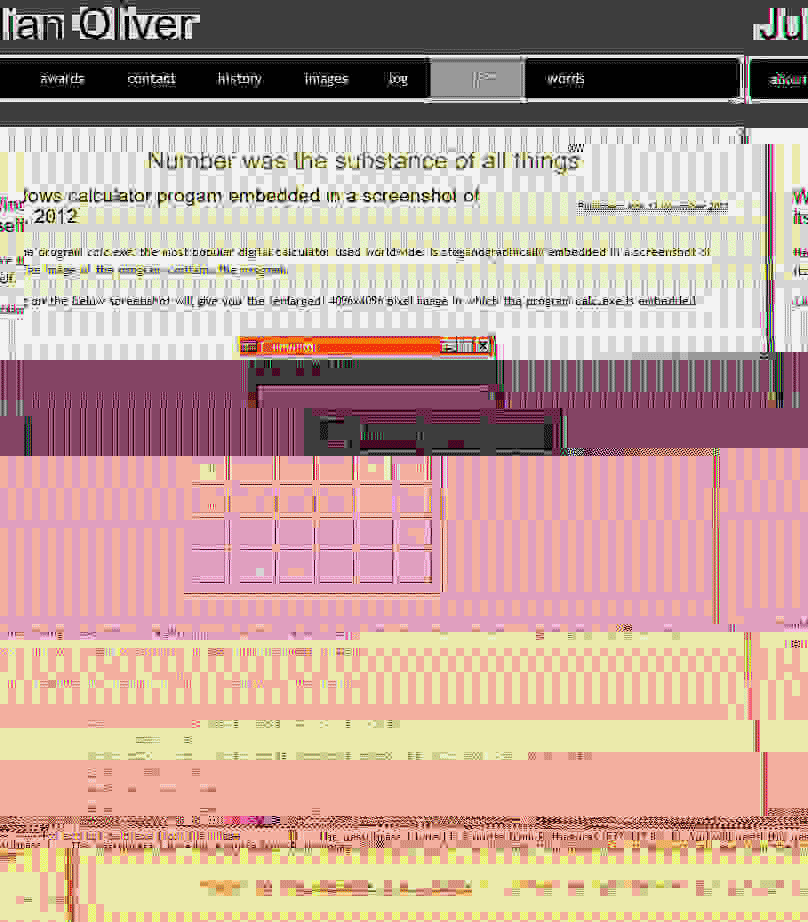
Number was the substance of all things is a 2012 project by Julian Oliver. On his website he describes it as follows:
Here the program calc.exe, the most popular digital calculator used worldwide, is steganographically embedded in a screenshot of itself. The image of the program contains the program.
https://julianoliver.com/output/number-was-the-substance-of-all-things.html
The tool he uses, steghide, is a steganography program that is capable of hiding data in various types of image and audio files.
The main functionality is to hide text or files in the already existing bytes of an image or audio file.
The whole thing happens with a random number generator and encryption.
This makes it practically impossible to extract the hidden data without knowledge about the hidden file and without the password for the encryption.
The bytes of the image file are also the bytes that make up the hidden file. It depends only on the program that reads the bytes.
If the program knows the correct structures, one or the other file can be read from the bytes.
With steghide and the correct password, the information can be displayed:
"calc.jpeg":
format: jpeg
capacity: 157.1 KB
Enter passphrase:
embedded file "calc.exe":
size: 222.5 KB
encrypted: rijndael-128, cbc
compressed: yes
Therefore the question arises, what the file actually is. A picture of a program or the program itself?
The question cannot be answered definitively, because it basically depends only on the correct perspective.
In the memory of the computer are the ones and zeros.
Any further classification into files, programs, images and so on, is done by a system.
This opens up not only fundamental problems of media theory, but also the question of what files actually are and how they are processed.
A file has a beginning and an end, otherwise it could not be clicked on the desktop, for example.
This means that there must be some kind of notion of it in the operating system.
A structure that ensures that a file can be opened and thus processed in the right way.
___ __ ___ __ __
|__| |__ /\ | \ |__ |__) /__`
| | |___ /~~\ |__/ |___ | \ .__/
This information about itself, usually at the beginning of a file, is called a header. They determine the structure of the file and provide information about how the file should be read and structured.
To examine the bytes of files, a hex editor can be used. This is a program which simply makes the contained bytes visible. Hex because the bytes are usually displayed in hexadecimal notation.
00000000 ff d8 ff e0 00 10 4a 46 49 46 00 01 02 01 00 77 |......JFIF.....w|
On the left is the position of the bytes and on the right the output in ASCII.
The magic bytes of the JPG file are \xFF and \xD8. In a part of the header you can read the letters JFIF.
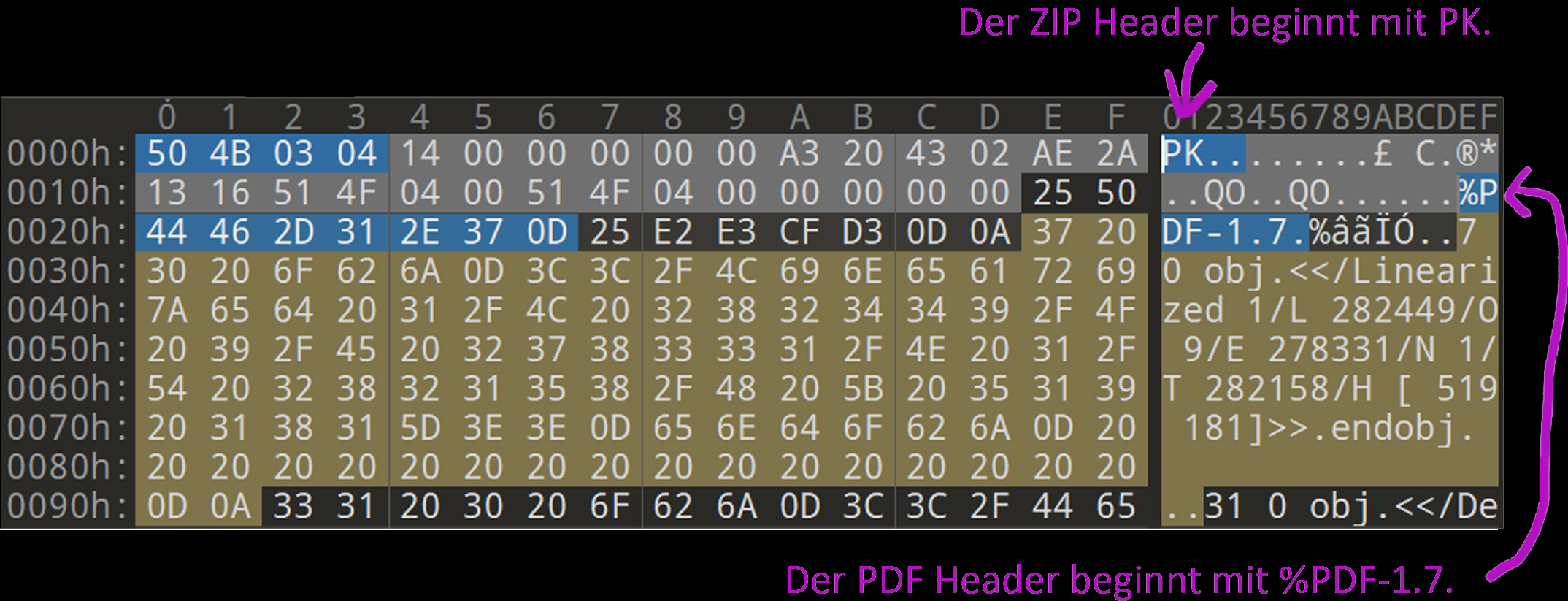
The beginning of a PDF file and a ZIP file can look like this:
00000000 25 50 44 46 2d 31 2e 36 0a 25 e2 e3 cf d3 0a 33 |%PDF-1.6.%.....3| ----------------------------------------------------------------------------- 00000000 50 4b 03 04 14 00 00 00 08 00 86 88 7a 51 6e 94 |PK..........zQn.|
__ __ __
/ ` |__| /\ |\ | / _` | |\ | / _`
\__, | | /~~\ | \| \__> | | \| \__>
__ ___ ___ __
|__) \ / | |__ /__`
|__) | | |___ .__/
The header of a Windows bitmap image file (.bmp) is usually 54 bytes long. This is followed by another block of information about the file and then the actual image data. The pixel values are written to the file one after the other without compression, depending on the color channel. A 5x5 pixel white BMP file looks like this in the Hex Editor:
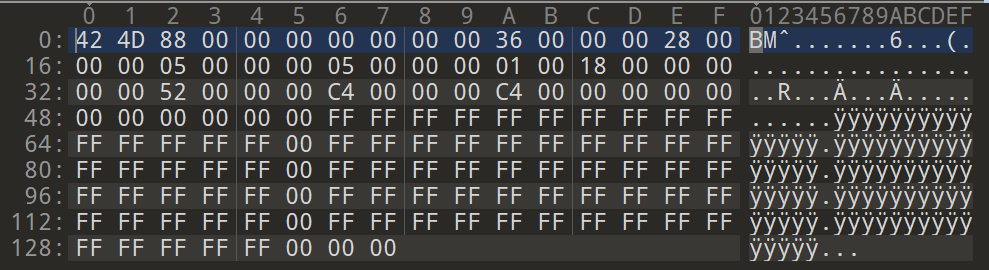
The hexadecimal values FF FF FF show that the pixels are all white. If the values are changed, a new image can be created. In the hex editor the bytes can be easily rewritten. For example, instead of FF, AC or AB can be written. The originally white pixels are now processed as pixels with the corresponding color value, which is calculated from the new bytes.
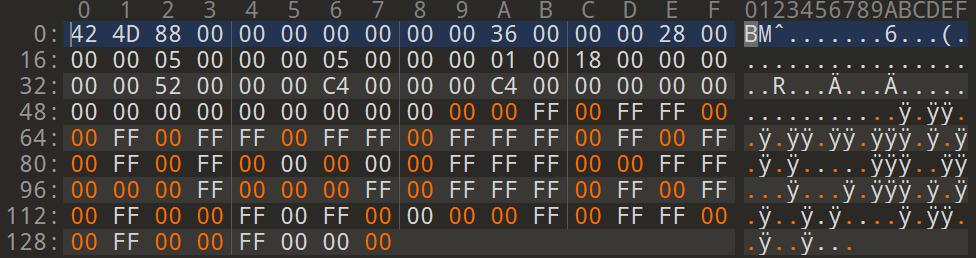
The changed values are marked here in orange. The structure of the content has been changed,
but the header, which describes the structure of the file, has not.
It must not be changed in this case, otherwise no image program would still recognize the file as a bitmap image.
With the correct header, however, a display program recognizes that it is a bitmap file and goes through the bytes in the contents in order.
The result of the changed formerly white pixels looks very colorful in this case:
![]()
So the program doesn't seem to care what values the pixels have, they are simply read, processed and displayed in order.
The main thing is that they fit into the structure that is to be processed.
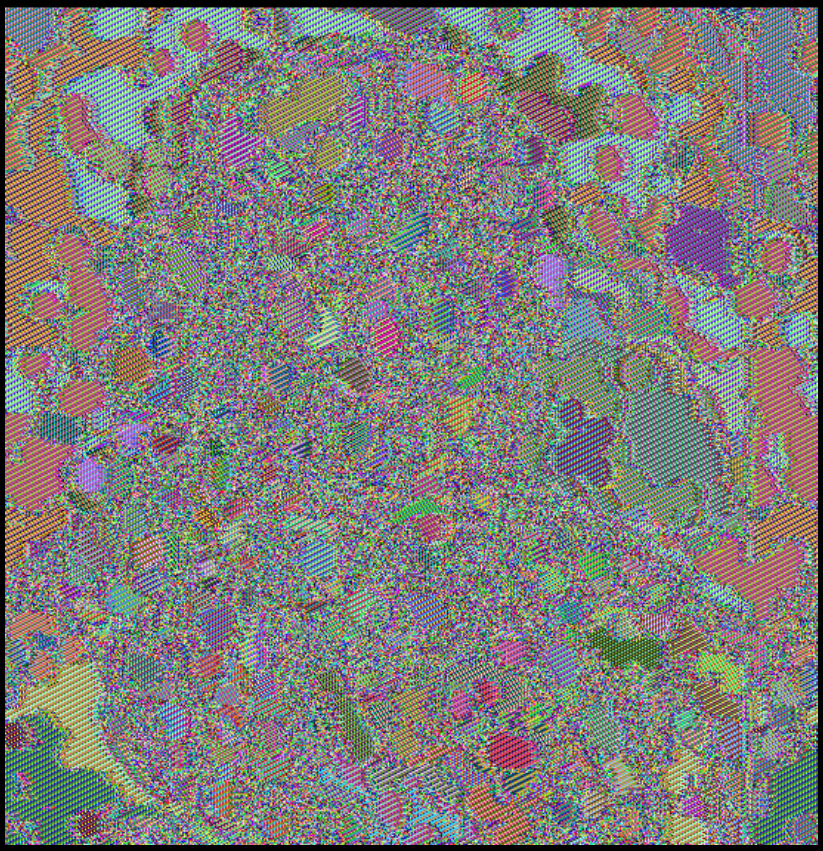
Editing the bytes in image files can create interesting glitches.
This is because the previous structures are ignored.
However, the system processes according to old patterns and so it seems that the elements have "slipped" and are no longer placed correctly...
__ ___ __ / _` | | | / ` |__| \__> |___ | | \__, | |
A glitch, in the context of digital signals, is a distortion that, among other things, causes artifacts to form in images or videos. These can be colorful or differently colored boxes and patterns that often make the viewer aware of how fragile and unreliable the digital data and transmissions are. Glitch art can therefore also be understood as a kind of media critique. Apart from that, deliberately staged and artistically provoked glitches offer a very unique aesthetic.
Applied directly onto the architecture of the building, the glitch misaligns the elements of the façade, bringing disturbance to an otherwise settled structure.
https://wwwwwwwwwwwwwwwwwwwwww.bitnik.org/h3333333k/
In their work H3333333K from 2015, the !Mediengruppe Bitnik transferred the phenomenon of glitch to the facade of the House of Electronic Arts in Basel. On the website of their project, they write that the glitch refers to current art production, which is about reflecting on its underlying technological and social conditions. It also alludes to the intrusion of chance, temporality, and playfulness caused by faulty data transmissions. The glitch, normally a very short-lived digital phenomenon, is here transported into a long-term work of art, set in stone, so to speak.

__ __ __ ___ __
/ ` |__) \ / |__) | / \
\__, | \ | | | \__/
__ ___
/\ |__) |
/~~\ | \ |
Recently, we have been hearing more and more about so-called crypto art in the art scene.
This refers to the possibility of verifying the authorship of digital artworks by means of blockchain technology.
In this way, digital works of art are supposed to gain a new market value. The word crypto is derived from cryptocurrency.
However, the word crypto has another meaning and can also stand for cryptography, i.e. encryption.
Encryption ensures the confidentiality of data.
This is usually done by encrypting a file with a password.
Of course, a password that is easy to guess does not provide reliable protection.
But cryptographic algorithms can also have weaknesses on their own.
In many cases, the Advanced Encryption Standard (AES) is used to encrypt data.
This encryption method in turn has various operation modes.
One of these is the Electronic Code Block Mode (ECB).
In this mode, the bytes of the file to be encrypted are divided into blocks of equal size, which are then encrypted with the key.
This means that the same blocks are encrypted in the same way even after encryption.
Thus, despite encryption, structures can become visible to a certain degree that allow conclusions to be drawn about the original data.
This is also the reason why this mode is generally regarded as insecure and is not recommended.
The weaknesses of the ECB mode combined with the just shown properties of the BMP files can create but visually interesting glitches.
For this only the original header of the BMP file must not be encrypted.
The rest of the encrypted image file is processed by the correct BMP header as pixel values, although it is actually the encrypted bytes.
The structures are recognizable because the AES-ECB algorithm turns the same colored areas into the same encryption blocks .
Here is the bash script for a crypto artwork that is not baked into the resource-wasting blockchain and can be copied as you like.
It's name is: Rembrand in AES-ECB-128.
Also check out this for more Crypto-Art
wget https://upload.wikimedia.org/wikipedia/commons/3/3e/↵ Johannes_Wtenbogaert_by_Rembrandt_van_Rijn.jpg -O rem.jpg convert rem.jpg -quality 10 t1 && convert -resize 30% t1 t2 convert t2 t3 openssl enc -aes-128-ecb -e -in t3 -out enc -K 00000000 head -c 54 rem.bmp > header dd if=enc of=bytes skip=54 cat header bytes >> rembrand-ecb128.bmp rm header bytes enc t1 t2 t3
___
|__ | | |\ | |__/ \ /
| \__/ | \| | \ |
___ ___
|__ | | |__
| | |___ |___
___ __ __ ___ __
|__ / \ |__) |\/| /\ | /__`
| \__/ | \ | | /~~\ | .__/
First, you must realize that a file has no intrinsic meaning. The meaning of a file - its type, its validity,its contents - can be different for each parser or interpreter.
https://www.alchemistowl.org/pocorgtfo/pocorgtfo07.pdf
Ange Albertini takes the game with file formats and their headers and byte structures to the extreme.
He also calls his byte arrangements schizophrenic files, since they are read differently by different parsers and thus one and the same file is interpreted as different files.
Whereas the correct term for a so-called multiple personality would actually be dissociative identity disorder.
The illness schizophrenia is often misunderstood and wrongly associated with the idea of multiple personalities.
Medically, however, schizophrenia rather describes a kind of episodic, paranoid delusional state.
Programs that unpack ZIP archives, for example, are usually written in such a way that they do not care where the ZIP headers are located.
They simply go through the file byte by byte until the correct bytes are found.
This leads to the possibility of writing a zip file inside a JPG file.
The program displaying the image reads from the beginning of the file, which correctly contains a JPG header,
to the place specified in the structure as the end of the JPG image, and does not notice that there is still a ZIP file hidden right behind it.
On the screen the image is displayed normally.
Nevertheless, the file can also be unpacked as a ZIP.
Thus, under the guise of a supposedly harmless JPG file, additional files can be hidden in the ZIP archive.
Also some PDF readers are quite flexible about this and allow the PDF headers to appear somewhere in the first 1024 bytes of the file.
What precedes this can therefore be used for other file headers, for example a ZIP file.
This means that a file can be a PDF and a Zip file at the same time, depending on which program reads it and which headers it looks for.
The following image shows nested headers of a ZIP file and a PDF file.
The header of the PDF file is written into a header field of the ZIP file that is not important for processing.
__ ___ ___ __
|__) \ / | |__ | | /\ /__`
|__) | | |___ |/\| /~~\ .__/
___ ___ __ __ __ ___ __ ___
| |__| |__ /__` | | |__) /__` | /\ |\ | / ` |__
| | | |___ .__/ \__/ |__) .__/ | /~~\ | \| \__, |___
__ ___ ___ __ __
/ \ |__ /\ | | | |__| | |\ | / _` /__`
\__/ | /~~\ |___ |___ | | | | | \| \__> .__/
Now, finally, all these techniques are to be combined once again for this part and, at the same time,
reference is to be made to the project by Julian Oliver mentioned at the beginning.
The following is to be understood as a not quite seriously meant, tongue-in-cheek homage to Number was the substance of all Things,
but without the calculator, because it is to be saved for this work.
Below you can download an animated GIF file.
This file is a screenshot of Julian Oliver's Number was the substance of all things project description on his website.
By manipulating the bytes, a glitch aesthetic was created.
The file is also an encrypted ZIP archive and can be decrypted with the password "Byte was the substance of all things."
The ZIP archive contains a PDF file on which the Critical Enigineering Manifesto can be read.
This file is also a JPEG image file with the Twitter profile picture of Julian Oliver himself.
calc.gif
|
└── archive.zip
|
└── manifesto.pdf
|
└── julian.jpg